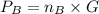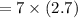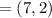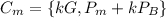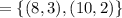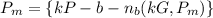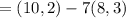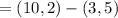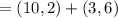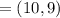This problem performs elliptic curve encryption/decryption using the scheme out-
lined in secti...

Computers and Technology, 02.01.2020 20:31 himatasy
This problem performs elliptic curve encryption/decryption using the scheme out-
lined in section 10.4. the cryptosystem parameters are e11(1,6) and g = (2,7). b's
secret key is nb = 3. (hint: note the relationship of this system to the one discussed in
the previous question (10.14)]
a. find b's public key pb.
b. a wishes to encrypt the message pm = (10,9) and chooses the random value
k = 4. determine the ciphertext cm.
c. show the calculation by which в recovers pm from cm.
(10.> for e11(1,6) consider the point g=(2,7). compute the multiple of g from 2g through 13g.)

Answers: 1


Another question on Computers and Technology

Computers and Technology, 21.06.2019 18:30
Given the following code: if (n == 2) { k -= 2; } else if (n == 3) { k -= 3; } can be rewritten as: if (< condition > ) { < assignment statement > ; } assume that evaluating < condition > does not change the values stored in n and k. which of the following could be used as < assignment statement > ? k -= n; k -= 1; k -= 2; k += n; k = n - k;
Answers: 2

Computers and Technology, 22.06.2019 14:30
Hi plz 11 ! when planning a table, what step comes first: "define the column headers" or "calculate the number of columns/rows"? a. calculate the number of columns/rows b. define the column headers
Answers: 1

Computers and Technology, 23.06.2019 14:30
Select the correct answer. which step can possibly increase the severity of an incident? a. separating sensitive data from non-sensitive data b. immediately spreading the news about the incident response plan c. installing new hard disks d. increasing access controls
Answers: 2

Computers and Technology, 24.06.2019 14:30
When workers demonstrate patience, are able to manage there emotions, and get along with other employees, which skills are being displayed?
Answers: 1
You know the right answer?
Questions



History, 02.11.2019 21:31



Business, 02.11.2019 21:31






Mathematics, 02.11.2019 21:31





Arts, 02.11.2019 21:31


Mathematics, 02.11.2019 21:31

Mathematics, 02.11.2019 21:31

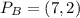 "(b) The ciphertext is "
"(b) The ciphertext is "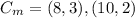 "(c) Between the two points, addition as well as multiplication are proceeding.
"(c) Between the two points, addition as well as multiplication are proceeding.