1.) Download the dataset named " Population. csv"
.2) Read data into Spyder
.3) Create vari...

Computers and Technology, 04.12.2021 05:20 deepunalli300p3ur3i
1.) Download the dataset named " Population. csv"
.2) Read data into Spyder
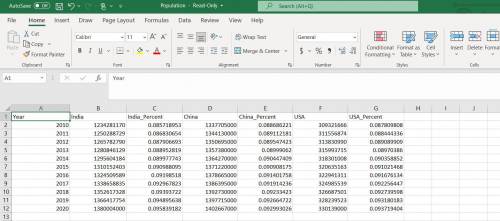
.3) Create variables for each column, each variable is going to store data from appropriate column of the “Population. csv” file (7 variables)
Make 3 scatter plots with axis, legend and Title labels for:
a) India by Year
b) China by Year
c) USA by Year

Answers: 2


Another question on Computers and Technology

Computers and Technology, 23.06.2019 03:10
Fill in the following program so that it will correctly calculate the price of the orange juice the user is buying based on the buy one get one sale.#include //main functionint main() { int cartons; float price, total; //prompt user for input information printf("what is the cost of one container of oj in dollars? \n"); scanf(" [ select ] ["%d", "%c", "%f", "%lf"] ", & price); printf("how many containers are you buying? \n"); scanf(" [ select ] ["%d", "%c", "%f", "%lf"] ", & cartons); if ( [ select ] ["cartons / 2", "cartons % 1", "cartons % 2", "cartons % price", "cartons / price", "cartons / total"] [ select ] ["=", "==", "! =", "< =", "> =", "< "] 0) total = [ select ] ["price * cartons", "cartons * price / 2 + price", "(cartons / 2) * price", "cartons / (2.0 * price)", "(cartons / 2.0) * price + price", "((cartons / 2) * price) + price"] ; else total = ((cartons / 2) * price) + price; printf("the total cost is $%.2f.\n", total); return 0; }
Answers: 2

Computers and Technology, 23.06.2019 11:00
What are the possible consequences of computer hacking? what is computer piracy? describe some examples. what are the effects of computer piracy? what are the possible consequences of computer piracy? what is intentional virus setting? describe some examples. what are the effects of intentional virus setting? what are the possible consequences of intentional virus setting? what is invasion of privacy? describe some examples. what are the effects of invasion of privacy? what are the possible consequences of invasion of privacy? what is an acceptable use policy and what is the purpose of the acceptable use policy what is intellectual property and how can you use it?
Answers: 1

Computers and Technology, 24.06.2019 13:30
Does anybody know how to hack into a google account? i had important information on it and it is gone now and i need getting it back.
Answers: 1

Computers and Technology, 25.06.2019 01:30
The study of how to design software, solve problems such as computer security threats, or come up with better ways of handling data storage
Answers: 1
You know the right answer?
Questions






Mathematics, 26.03.2021 01:10

Arts, 26.03.2021 01:10

English, 26.03.2021 01:10


Mathematics, 26.03.2021 01:10

English, 26.03.2021 01:10

Social Studies, 26.03.2021 01:10




Biology, 26.03.2021 01:10

Health, 26.03.2021 01:10






