Computers and Technology, 26.12.2019 22:31 samavants74
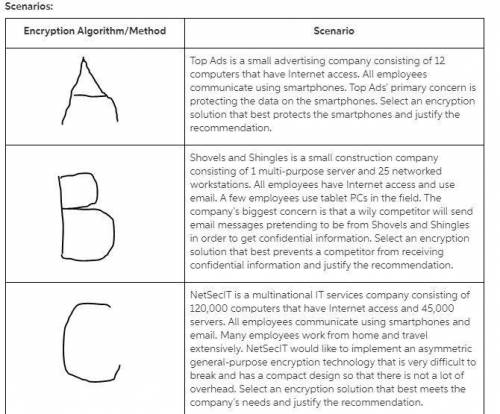
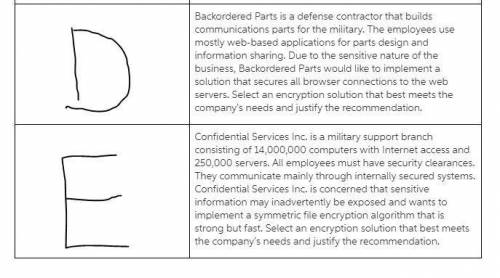
Match common encryption algorithms and methods with the scenarios representing real-world business applications and requirements. you may use the course textbook and the internet to research encryption algorithms and methods.
common encryption algorithms and methods:
data encryption standard (des)
rivest, shamir, and adleman (rsa) encryption algorithm
triple des
diffie-hellman key exchange
elliptic curve cryptography (ecc)
blowfish
secure sockets layer (ssl)
transport layer security (tls)
advanced encryption standard (aes)
digital signature

Answers: 2


Another question on Computers and Technology

Computers and Technology, 23.06.2019 07:10
If you want to import a picture into a dtp application, what must you do first? draw an image frame. import text. open the folder containing the file. select get image… from the windows menu.
Answers: 2

Computers and Technology, 23.06.2019 22:30
What would be the address of the cell, which is at the intersection of the second row and the third column in a worksheet?
Answers: 1

Computers and Technology, 24.06.2019 11:30
Convert 11001110(acdd notation) into decimal
Answers: 2

Computers and Technology, 24.06.2019 12:00
Match the function to its purpose. fast worth 50pts.
Answers: 1
You know the right answer?
Match common encryption algorithms and methods with the scenarios representing real-world business a...
Questions

Mathematics, 12.11.2020 23:20

Mathematics, 12.11.2020 23:20


History, 12.11.2020 23:20


Social Studies, 12.11.2020 23:20



Health, 12.11.2020 23:20

Mathematics, 12.11.2020 23:20

Mathematics, 12.11.2020 23:20

Mathematics, 12.11.2020 23:20

Mathematics, 12.11.2020 23:20




Mathematics, 12.11.2020 23:20

Geography, 12.11.2020 23:20

Mathematics, 12.11.2020 23:20